Reverse Engineering a Chinese USB Security Adapter
You should avoid connecting your USB devices to anything untrusted. And don’t use public USB charging ports – you never know, if charging is all they actually do. Always bring your own charger. However, when you travel, sometimes you don’t have options. For example, some airports or aircraft offer USB charging ports – but no mains sockets to plug your own charger...
If you really have to charge in those places, there is a simple solution: a USB cable or adapter, only connecting power, but blocking any data exchange.
Since no physical data connection exists, these adapters should make it safe to charge from an unknown USB port, at least avoiding the theoretical risk of your device being hijacked.
Offers on eBay & Co
There are tons of offers on ebay, AliExpress etc for such "USB data blocker adapters". They are made as simple USB-A to USB-A adapters. They connect power normally, but block any data transfers. At least that’s the idea.
I ordered one of these security devices on ebay. Less than $3, including shipping. Shipped directly from China. Took about a week.
Oh, yes, the combination of "ebay", "Chinese" and "security" may raise a few eyebrows. But what could go wrong with such a simple device?
Testing
I was suspicious, so I tested it first. I used an old device, connected its USB cable to the "data blocker adapter" and plugged the adapter into an old laptop.
Pla-pling!
A pop-up message: "New USB device connected!" - including the name of my device. That’s weird. How can it recognize the device type and name, when there is no data connection?
Maybe this security adapter is smarter than expected – allowing basic enumeration, just blocking actual data transfers? Nope. Transfer of data files also worked normally.
That is… not good!
"Reverse Engineering"
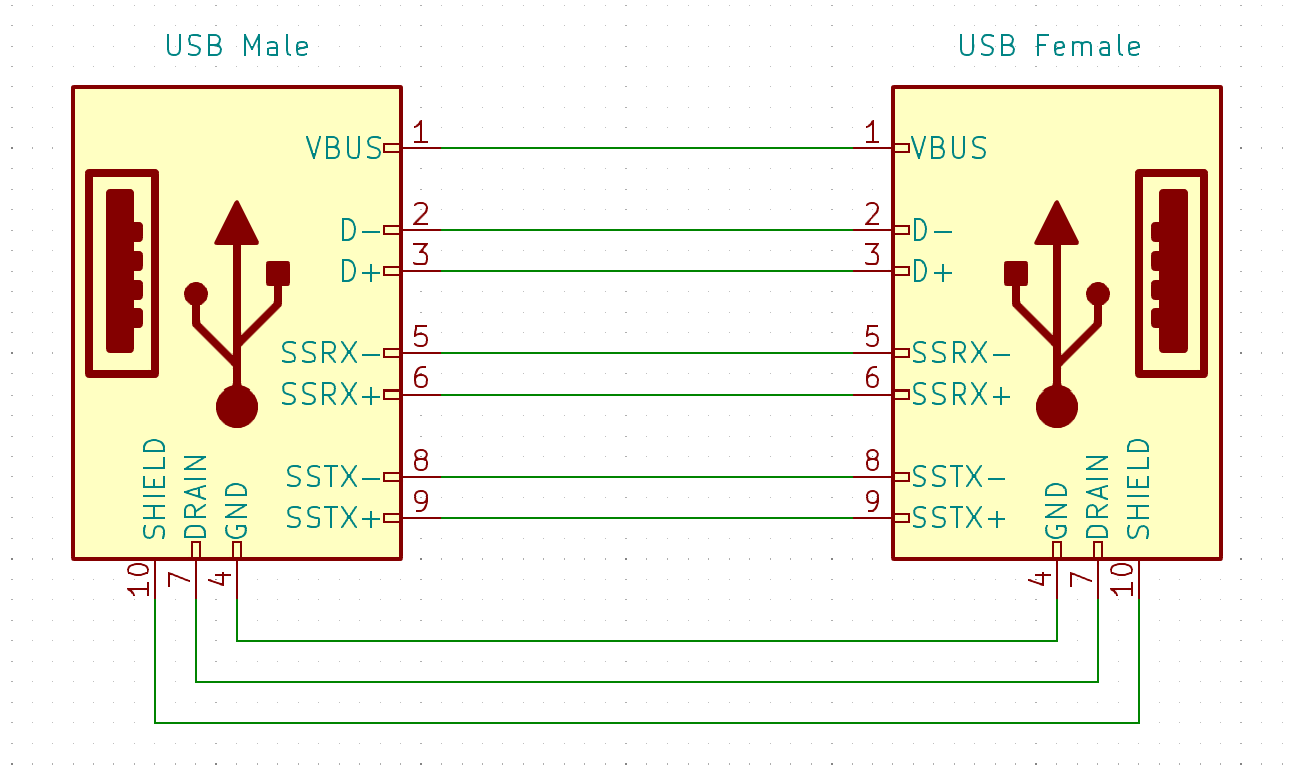
Time to get the multimeter... Took just a few minutes to determine the security adapter’s schematics:
So, it’s simple. It’s not only connecting power (GND and VBUS), but also the two differential D+ and D- data lines for USB 1.0/2.0 ("USB HighSpeed" at 480Mbit/s).
Even better: it also connects all extra USB3 signals. So it supports connections of up to the USB 3.2 standard "SuperSpeed+" (20Gbit/s). That would normally be a good thing. Except it defies the entire purpose of a "data blocker adapter".
That is a little... unexpected? … disappointing? … alarming? :)
So, this device is a complete fake. The only technical property that could be attributed to it is: it’s about a ½ inch extension of your USB cable. Nothing else.
eBay Complaint
I opened an "item does not match description" complaint on eBay, describing the problem. Took a few hours until the seller responded:
"Please send photo how device not match description."
Well, yeah, it *looks* alright.
Anyway, a photo and another copy of the problem description was enough. I got a refund. The vendor didn’t get away with his fake this time.
Opening the Adapter
Since the adpater wasn’t useful as it was, I opened it. Its aluminium shell could only be opened with destructive means.
The PCB was simple. I forgot to make photos, but just look at the schematics above. You don’t need advanced imagination to picture a tiny PCB with 9 traces - connecting 9 pins of the male USB connector to 9 pins of the female socket. Nothing else on the PCB. The connectors’ shielding was connected through the aluminium shell.
Hacking the Adapter
I used a small drill to cut the traces – except for GND and VBUS. So it now works as it was supposed to. Connects power but nothing else. I made a new makeshift shell with tape. It’s probably not going to last long, but maybe it will at least be useful once or twice.
Why?
This leaves the question: why? WHY? Why did they make a fake adapter – when they could have made it to work as described for exactly the same cost - just with fewer traces on the tiny PCB?
It’s puzzling. But here are the reasons I could think of. Add a comment below which option you think is most likely, or if you have another idea:
Option A:
They don’t even know what they are doing. Nor do they care. It was just made to look like some other ebay offers. Connecting all connector pins was the best the "engineer" could come up with.
Option B:
It was an honest mistake: the ebay seller grabbed the wrong adapter from the wrong box. (Which of course doesn’t explain why a box with such absolutely useless devices should exist in the first place).
Option C:
"For technical & economic reasons". Indeed, I could think about one reason how these fake adapters came into existence.
Originally they maybe sold genuine "data blockers" - years ago. That was easy and all was good with original USB 1.1 / 2.0. Those devices don’t need anything except GND/VBUS to charge normally.
Then USB3 / USB-C was invented with the "Power-Delivery" (PD) feature.
This feature is what allows fast-charging these days. It supports different voltage levels: 5V, 15V or 20V. Recently the PD standard was extended to also support 28V, 36V, and 48V (mostly for laptops).
Power-Delivery requires the devices to communicate in order to exchange capabilities. The charger announces what power levels it’s able to deliver, the device announces the voltage levels it’s able to accept and the current level it would like to draw. The charger may then safely switch to a higher output voltage matching the device. And it may raise its output current limitation. PD currently supports different levels of up to 5A.
Of course, PD requires the USB data signals to be connected – otherwise the charger and device cannot agree on a higher voltage/current - and you are stuck with 5V (and often a maximum of 900mA). Genuine "data blockers" may have caused quite a few complaints by (ebay) buyers expecting their modern phones to keep fast-charging.
And there are only two basic ways to restore fast-charging / Power-Delivery with these adapters:
(1) Either reconnect all USB connector pins, so PD works normally – while, of course, any other communication is also no longer blocked.
(2) Make an adapter which intercepts the low-level USB protocol. It needs to allow the exchange of all PD messages, while blocking all other "high level" data messages.
Option (1) is easy & doesn’t cost anything. No more complaints about missing fast-charging. Just results in selling a totally useless/fake product as a side-effect...
Option (2) involves real engineering & costs money.
It’s been my honor
Oh, after the refund, I got a final message from the ebay seller:
Sure thing. It was also my "honor" to be on the receiving end of a fake product sale… :)
- MacFly's blog
- Log in or register to post comments






Comments
Are there data blockers that
Are there data blockers that support USB PD?
saver
They may not be absolutely useless: a common accessory for commercial equipment is the "connector saver". They are made for D-subminiature, as well as circular MIL, and RF connectors.
Whether these USB male-female plugs are any good at saving connectors depends on their physical precision, plating, etc.
Tom Owad wrote:Are there data
I'm not sure, but I doubt it. It would require a dedicated chip or at least a microcontroller to forward the PD, but filter the data messages. And then it would leave the question if you trusted this chip (or the microcontroller firmware) to be secure and not get hijacked itself. Or worse: when you bought the adapter from a dodgy source (like me), how do you know that the microcontroller on the "security adapter" itself wasn't doing something weird to your phone?
That was the beauty of the original "data blocker" concept, which just connects the two power pins: the idea was dead simple, you could easily verify it, and it was basically guaranteed to be safe.
Great analysis MacFly, how
Great analysis MacFly, how funny. Only trust those kind of things in a transparent case!
Add some protection
I would also want such an adapter (without data lines connected) to have some kind of 5 Volt Transzorb Diode to protect my device against any faulty/rogue/zapping chargers trying to destroy my device...
Yes, zapping is another
Yes, zapping is another threat. Zappers easily generate spikes of several thousand volts. A simple diode may not be enough for protection. Zappers, however, wouldn't remain unnoticed - especially in places which are frequently used (like at airports etc).
My makeshift adapter has seen its first use. And I wasn't arrested for connecting a suspiciously looking taped device to the onboard system...
USBBlocker2.jpg